Network Layer Protection
A programmable security perimeter for inbound and outbound traffic at the edge.
How it works
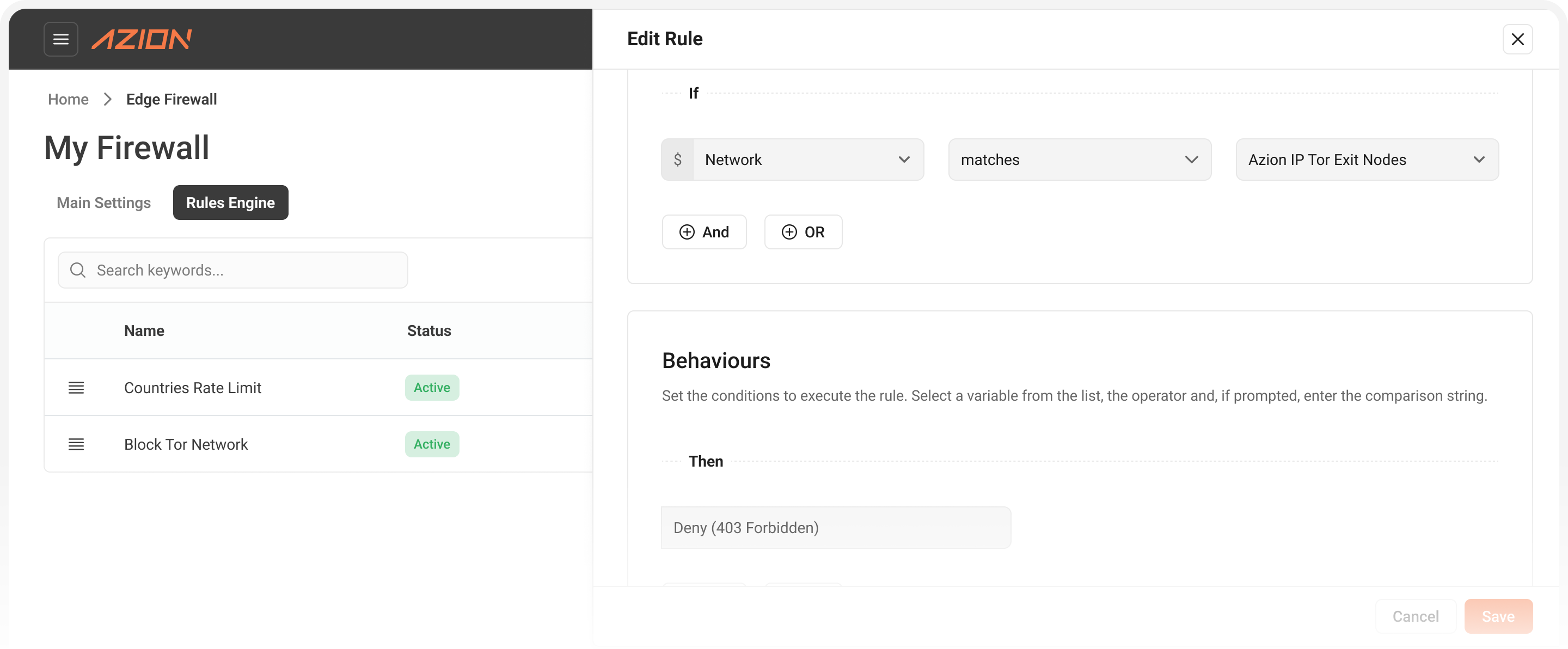
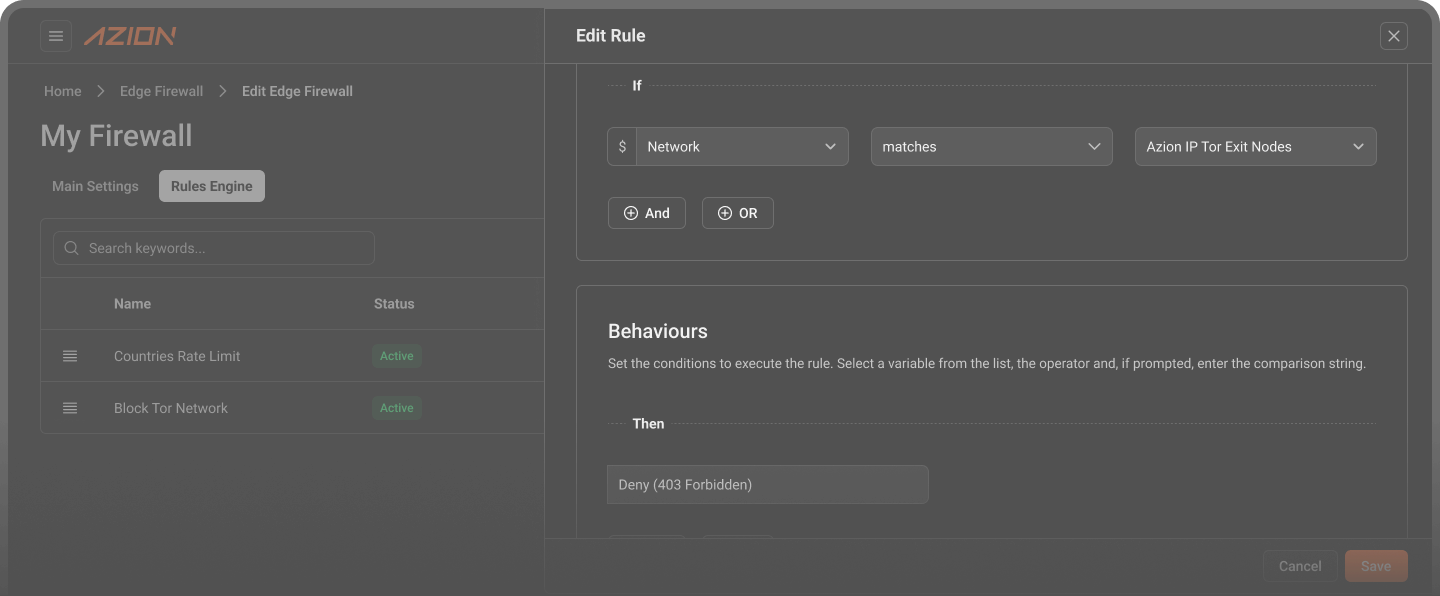
Network Lists for programmable ACLs
Network Layer Protection maintains network lists containing IP addresses, geographic locations, ASN data, and reputation information serving as criteria for Edge Firewall rules.
The system provides Azion-maintained lists including Tor Exit Node IPs and Origin Shield addresses automatically updated for security and infrastructure protection.
Custom network lists enable organizations to create IP allow/block lists, geographic restrictions, and reputation-based filtering tailored to specific security requirements.
Segmented security through rule-based traffic control
Edge Firewall rules reference network lists to apply different behaviors including Deny, Drop, or Set Rate Limit based on network criteria combined with other conditions.
The platform enables geographic segmentation allowing region-specific access controls while supporting legitimate traffic like search engine crawlers through complex rule logic.
Multiple Edge Firewalls can reference the same network lists ensuring consistent security policies across applications with automatic propagation of list updates.
Threat response through automation
Network Layer Protection events stream to SIEM platforms enabling automated incident response where external systems can update network lists via API based on threat intelligence.
The system supports programmatic access through Edge Functions allowing custom security logic to query network lists and implement dynamic blocking decisions.
Real-time list updates automatically reflect across all associated Edge Firewalls and applications without manual intervention or service disruption.
Learn how you can benefit from our platform
Enforce network lists
Protect your applications against Tor networks
Stop account takeovers
Set rate limits to limit excessive login attempts from brute force or credential stuffing
Stop abusive users or attackers
Create watch lists and tag events to monitor the user's behavior
Protect your origin
Hide origin servers from the open Internet to keep your apps safe and performant
Avoid bandwidth costs
Reduce bandwidth costs by eliminating undesired traffic spikes or attacks
Trusted by market leaders across banking, e-commerce, tech, and other industries.
Advanced mitigation
Full protection for your applications, content and infrastructure with network lists, rate limiting, and origin shield.
Flexibility
Protect your applications, APIs and networks - wherever they are hosted - multi-cloud, on-premises or hybrid.
Granular control
Create block lists based on networks (ASN), IP/CIDR, country or automatically updated lists, which include Tor networks.
High resiliency
Automatically-tuned, software-defined network routes bad traffic away, backed by our 100% SLA.
Rapid response
Mission-critical support and expertise before, during and after an attack.
Lower bandwidth costs
Block bad traffic at the edge - without having to scale up bandwidth.
Observability and automation
Define responses and gain valuable insights into specific URLs of websites, applications, or API endpoints.
”Azion guarantees availability for the Brazilian omnichannel bank and its 1M+ customers by protecting it from multi-layer DDoS attacks.”
Sign-up and get $300 to use for 12 months.
Access to all products
No credit card required
Credit available to use for 12 months