In the digital age, one of the most common questions for organizations is: how to guarantee data protection?
With the growth of devices connected to the Internet worldwide, the risks related to the loss of personal and business data are latent. This, in turn, could bring severe consequences for organizations, such as the exposure of personal or financial information, damage to reputation, or even non-compliance with regulations and laws.
Just a few years ago, in 2020, the world had 14 million devices, and forecasts point to more than 18 million by 2025. So information security is a central issue.
The reality is that prevention is more important than trying to stop a leak when it’s already happening, which is why solutions such as Data Loss Prevention (DLP) are shown as one of the resources that provide more visibility and protection for data currently.
In this article, we’ll explore what Data Loss Prevention is and how to protect your company from data loss.
What is Data Loss Prevention?
According to Gartner, DLP is “a marketplace of technologies that includes offerings that provide visibility into the use and movement of data within an organization.”
DLP helps organizations protect their confidential and critical information against data-related threats, such as risks of unintentional or accidental data loss and sensitive data exposure.
One of the objectives of DLP is to prevent data exfiltration, that is, to avoid the unauthorized exit of valuable or confidential data from an organization to a place external to it. For example, via e-mail or instant messages.
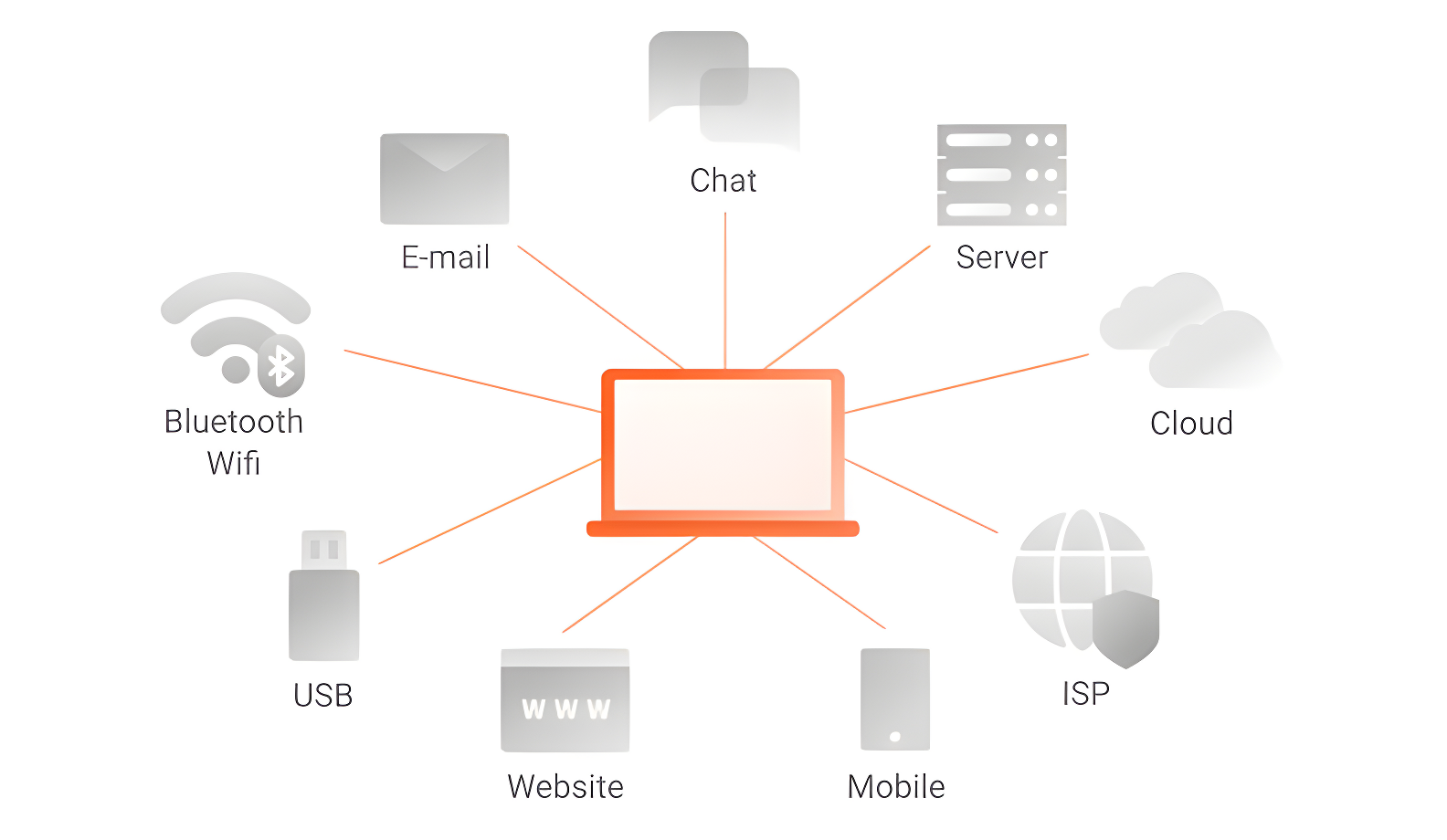
DLP uses monitoring, alerting, warning, blocking, and other remediation tools and may include techniques such as:
- Data identification and classification
- Data monitoring
- Encryption
- Security policies
What to Expect From a Data Loss Prevention Solution?
A proper DLP solution should provide the ability to reduce risk to your most critical assets, monitor application data, and mitigate high-risk communications while maintaining legal compliance.
Cloud computing platforms allow you to implement DLP practices for websites and applications based on detecting confidential information, analyzing content in depth, and configuring tools that help you detect content according to your business data privacy protection policies.
An efficient DLP solution can cover two essential aspects:
1. Data security: It protects access to confidential information and creates a security perimeter through:
- Inspection of HTTP traffic regarding confidential data (restricts extensions, HTTP methods, among others)
- File exclusion
- Restrictions and control of user permissions to devices, domains, and networks for sensitive data
- Filtering by words in BODY, PATH, and Headers (it searches for certain words or phrases and blocks them)
- Definition of a number of requests
2. Visibility: A DLP solution must provide a complete view of an organization’s data through:
- Traffic monitoring in real time
- Fault identification
- Implementation of the business rules that best adapt to any technology
- Information classification
- Automation to prevent data leakage
- Provision of logs and event control
DLP Use Cases
Compliance
DLP solutions allow companies to apply policies to sensitive data on devices or across the entire network and ensure its security.
Organizations must comply with government regulations, such as privacy and data protection laws, as well as regulations in the financial sector.
DLP is an ally of the security team, and today it’s a requirement for information access control. An implementation based on the access flow and real-time data monitoring guarantees the necessary resources to control access to information.
Data Leak
Preventing data leak or exfiltration is one of the main goals of DLP. This implies that it’s possible to issue alerts, identify sensitive data, and apply restrictions to unauthorized users when there is a risk of leaving an internal network or being revealed on a website or application.
Protection of Sensitive Documents
DLP can help protect the financial and personal information of a company’s customers, such as credit card numbers and social security. It alerts when this information is moved, copied, or shared across devices or networks.
Conclusion
DLP is a set of technologies and practices that can certainly help protect an organization’s sensitive information. Implementing a robust DLP solution at the edge of your network can provide better security, reduced latency, and more effective protection against data exfiltration attempts.
If you want to get the benefits of this, learn about Azion’s web platform that are helping companies to protect their data:
-
Rules Engine: an ally of the Network Layer Protection solution, creates access to confidential information and a security perimeter, blocking HTTP methods, paths, headers and filtering by GEOIP.
-
Origin Shield: Creates a security perimeter between the edge and the APIs, allowing only traffic coming from Azion.
-
Real-Time Metrics and Data Stream: Provides detailed Insights with an efficient real-time visualization of the performance, availability, and security of your applications.
As organizations continue to manage increasing amounts of sensitive data in an ever-more connected world, data loss prevention will remain a critical component of any comprehensive cybersecurity strategy.