Fastest distributed network in the planet
+120 points of presence across the globe so your data and application are where your users are
Hyperconnection expressed in numbers
30ms
to reach anywhere in the Americas and Europe
3.3k+
ASNs directly connected to the Azion network
100%
availability, guaranteed by SLA
100+
Edge Locations worldwide
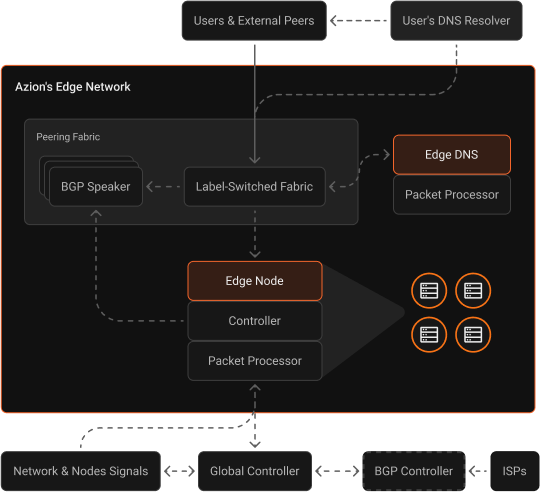
The network with best performance, availability, and resiliency
Our highly distributed architecture includes edge nodes strategically located inside ISPs' (Internet Service Providers) last-mile networks and connectivity to multiple IXPs (Internet Exchange Points), private and public peerings, and Tier 1 transit providers around the world.
Native DDoS protection
The mission to create a safer and more reliable Internet is a core value for us. To promote this, we are also working with other market players on the Internet Society's MANRS (Mutually Agreed Standards for Routing Security) initiative.