Programmable security modules and rule processing
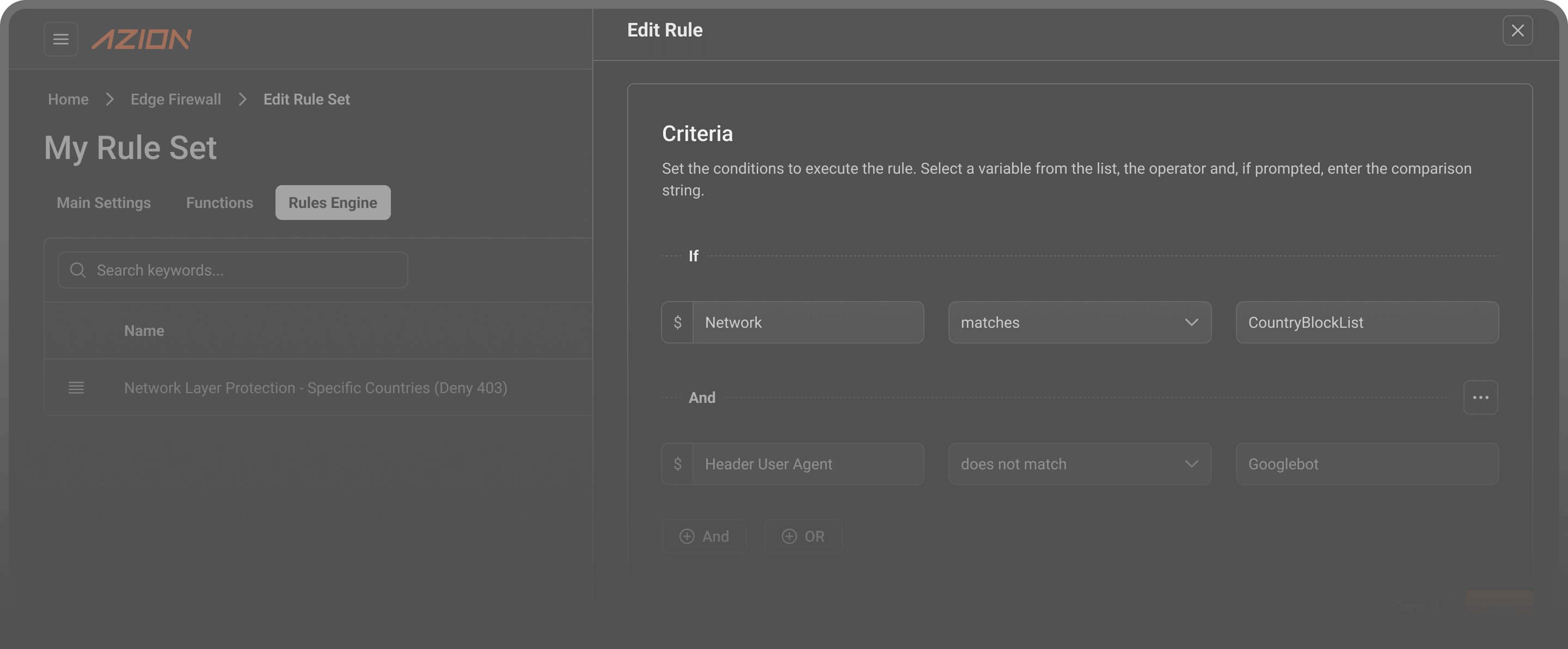
The Firewall processes incoming traffic at OSI layers L3-L7 using configurable criteria and behaviors defined in the Rules Engine.
The system evaluates requests against user-defined conditions including headers, cookies, query strings, and network parameters.
Rules execute sequentially with conditional logic, allowing precise control over traffic before application access.

Firewall Functions and security integrations
The Functions runtime executes custom JavaScript security code and third-party marketplace integrations directly at global points of presence.
The system enables integration with specialized security solutions including authentication, JWT validation, fingerprinting, rate limiting, and payload validation services.
Configurable behaviors provide flexible response options including blocking, monitoring, redirecting, and custom status codes.

Distributed rule synchronization and SIEM integration
The platform automatically synchronizes configured security rules across all global points of presence through API-driven deployment.
Data Stream connectors enable forwarding of real-time security events to the customer's SIEM platforms for correlation analysis and threat intelligence feedback.
API endpoints allow dynamic adjustment of network lists and security configurations based on external threat intelligence and operational requirements.

Accurate threat detection and mitigation with programmable rules.
Web Application Firewall
Protect your applications against OWASP Top 10 threats, zero-day attacks, and more
Network Shield
Stop attackers with smart rules, network lists, rate limiting, and more.
DDoS Protection
Always-on protection against DDoS attacks, backed by a 100% SLA.
Trusted by security experts in banking, e‑commerce, technology, and other industries.
Protect legacy and modern applications/APIs
Protect attack surfaces against evolving web threats.
Always deliver the best experience to customers
Keep your applications, content, and origin infrastructure always available with our 100% SLA.
Compliance without complications
Simplify compliance with security standards like PCI-DSS and an intuitive high-level platform.
Implement DevSecOps processes
Ship secure applications at the right time.













