SECURE
Web Application Firewall
Enterprise-grade protection against OWASP Top 10 attacks, zero-day threats, and emerging vulnerabilities. Trusted by 20,000+ customers across 100+ global locations.
OWASP Top 10 coverage
attack detection accuracy
average cost reduction compared to others
Zero config DDoS built-in
Stop attacks before they reach your origin
Block malicious requests at distributed locations with global threat detection. Protect against SQL injection, XSS, RFI, and zero-day exploits with real-time intelligence and adaptive rule sets.
Significant cost savings
Pay only for analyzed requests with transparent usage-based pricing. No hidden fees, no infrastructure costs, no vendor lock-in.
Deploy in minutes, not months
Start protecting your applications immediately. No hardware to provision, no complex setup, no maintenance overhead.
Scale automatically with your traffic
Handle traffic spikes seamlessly with distributed global architecture. From startup to enterprise scale without configuration changes.
Optimize protection without breaking production
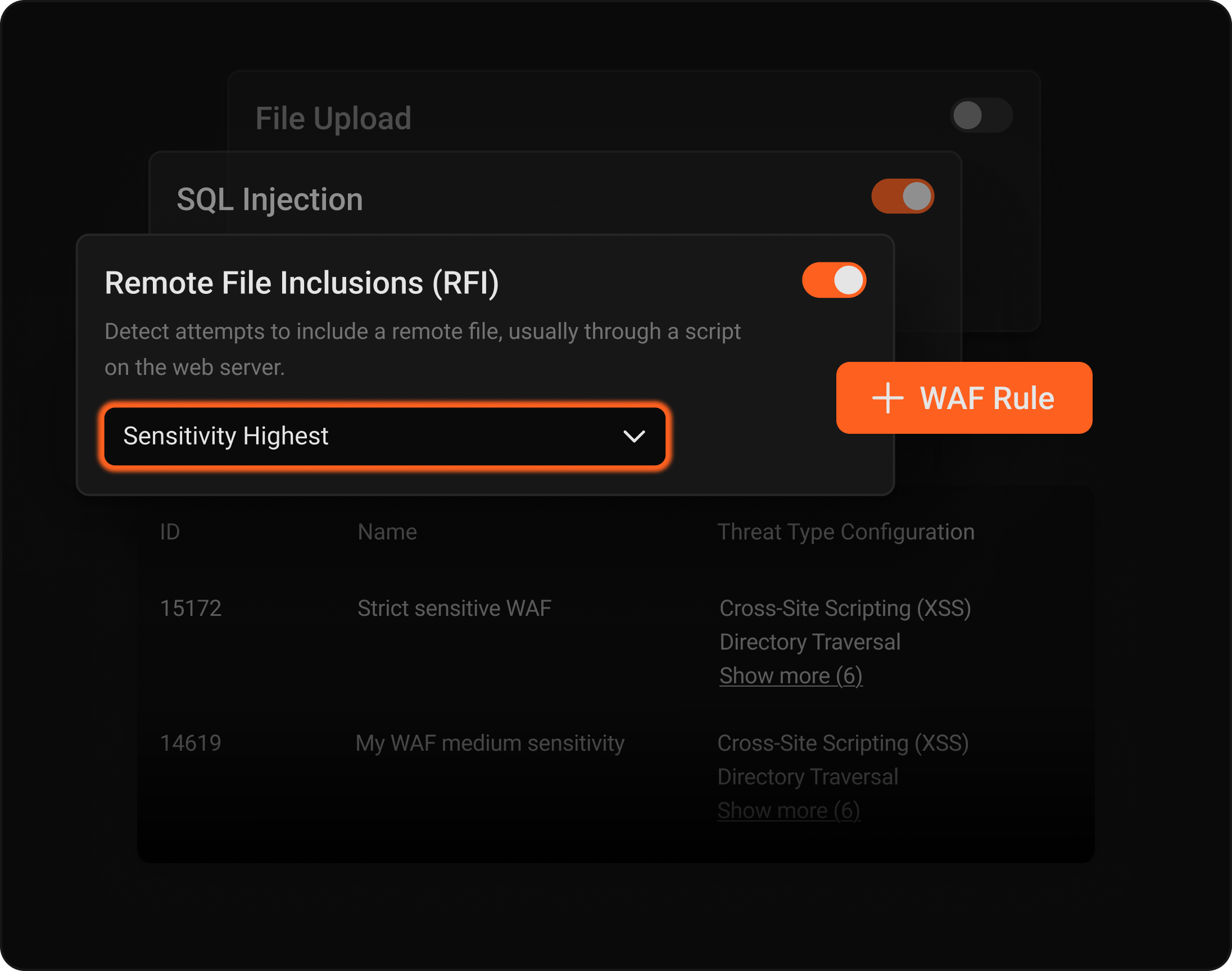
Switch between Learning and Blocking modes to eliminate false positives. Adjust sensitivity levels across five tiers and create custom exceptions without disrupting legitimate traffic.
Full visibility into security events
Stream security events in real time to your SIEM and analytics platforms. Get detailed threat intelligence, risk scores, and actionable insights for faster incident response.
Azion is recognized as a High Performer in the Web Application Firewall category in the G2 Winter 2026 Reports.
Rated 4.5/5 stars by security professionals worldwide for ease of use, performance, and customer support.

Security without complexity
Out-of-the-box protection with customizable rules
Enable preset rules for common attacks and adjust protection across five sensitivity tiers.
Run multiple WAF profiles per application to fine-tune what gets blocked.
Detect attacks faster than ever
Almost 99% of all events and logs are available in under 40 seconds in any interface APIs, GraphQL, dashboards and your SIEM using Data Stream.
Our proprietary distributed network is built to scale, and you security team must know immediately what is happening with your applications.
That's exactly what we provide.
Advanced threat analysis with intelligent risk scoring
Analyze HTTP, HTTPS, and HTTP/3 traffic with machine learning algorithms that score each request based on behavioral patterns and threat signatures.
Detect zero-day vulnerabilities and OWASP Top 10 attacks with precision. Use Learning Mode to tune rules and eliminate false positives before deploying to production.
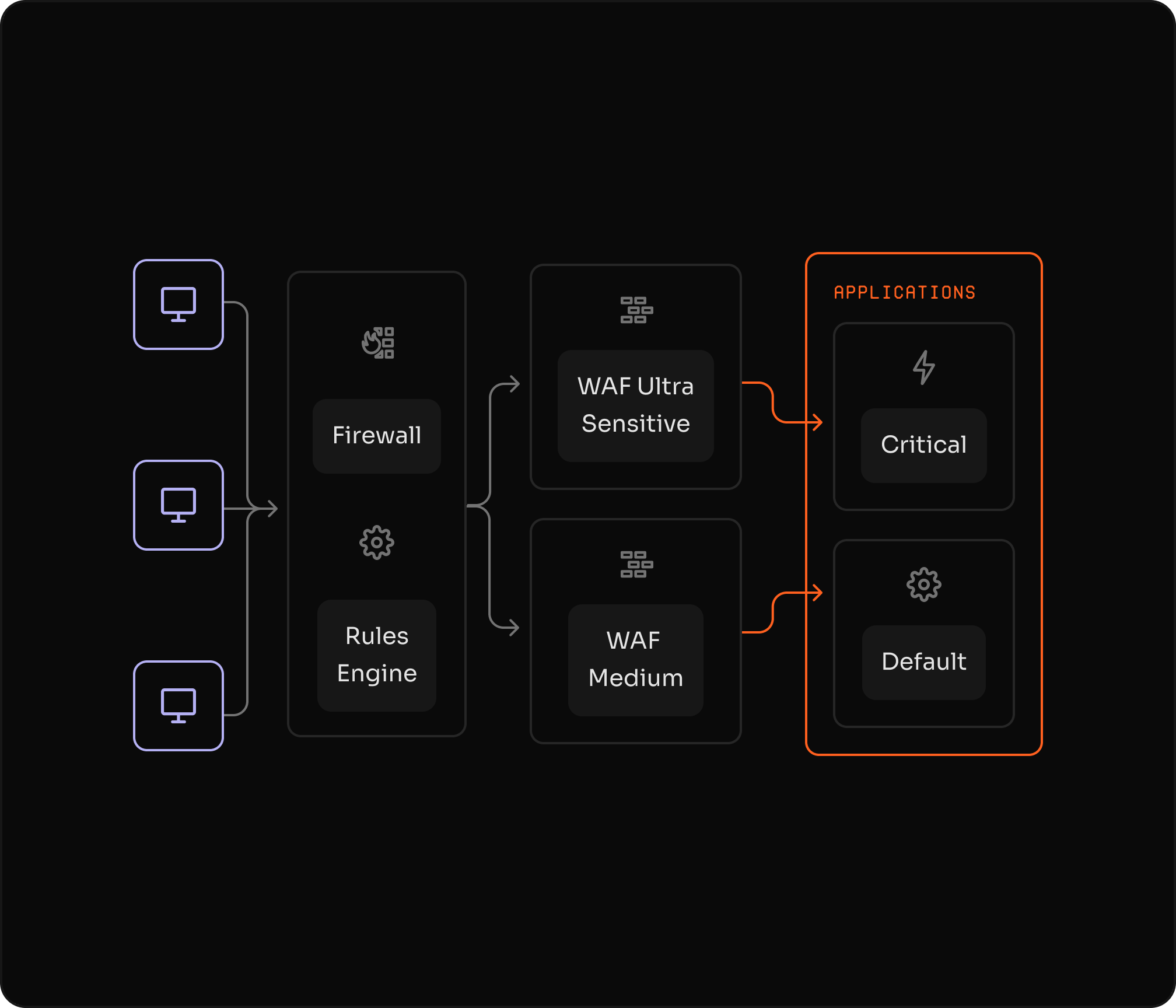
Real-time blocking, real-time visibility
Block threats instantly at distributed global locations before malicious requests reach your origin servers. Create Custom Allowed Rules to whitelist legitimate traffic patterns.
Stream security events in real time via Data Stream to your SIEM, Splunk, Datadog, or custom analytics platforms for enhanced visibility and automated incident response.

Protect serverless, traditional and hybrid applications
Frequently Asked Questions
I'm under attack. What should I do?
Your system is under attack right now? Get immediate expert help.
What happens next:
- Connect with our security specialists instantly
- Real-time attack analysis and threat identification
- Custom security rules deployed to block the attack
- Advanced protection activated immediately
Don't wait - every second counts during an active attack.
What is a web application firewall and how does it work?
A web application firewall (WAF) is a security solution that monitors, filters, and blocks HTTP/HTTPS traffic between a web application and the internet. It works by analyzing each request against a set of rules to detect and prevent attacks like SQL injection, cross-site scripting (XSS), and other OWASP Top 10 threats. Azion WAF operates at the application layer (Layer 7) on a globally distributed network, inspecting traffic before it reaches your origin servers with sub-10ms latency.
What is the difference between a WAF and a traditional firewall?
Traditional firewalls operate at the network layer (Layer 3-4) and filter traffic based on IP addresses, ports, and protocols. A WAF operates at the application layer (Layer 7) and understands HTTP/HTTPS protocols, analyzing request content, headers, cookies, and payloads to detect application-specific attacks. While network firewalls protect infrastructure, WAFs specifically protect web applications from threats like SQL injection, XSS, and zero-day exploits that traditional firewalls cannot detect.
How long does it take to deploy and implement a WAF?
Azion WAF can be deployed in under 30 minutes with no hardware provisioning or complex setup required. Simply configure your DNS to point to Azion's network, enable WAF protection in the console, and select your security rules. Start in Learning Mode to observe traffic patterns, tune sensitivity levels to eliminate false positives, then switch to Blocking Mode. Unlike traditional WAF solutions that take weeks or months to implement, Azion WAF provides immediate protection with minimal configuration.
Does Azion WAF protect against OWASP Top 10 vulnerabilities?
Yes, Azion WAF provides comprehensive protection against all OWASP Top 10 threats including SQL injection, cross-site scripting (XSS), broken authentication, sensitive data exposure, XML external entities (XXE), broken access control, security misconfigurations, cross-site request forgery (CSRF), insecure deserialization, and components with known vulnerabilities. Our rule sets are continuously updated with the latest threat intelligence and zero-day vulnerability signatures to protect against emerging attacks.
What types of attacks can a web application firewall prevent?
Azion WAF prevents a wide range of attacks including SQL injection, cross-site scripting (XSS), remote file inclusion (RFI), local file inclusion (LFI), command injection, path traversal, cross-site request forgery (CSRF), XML external entities (XXE), server-side request forgery (SSRF), and zero-day exploits. It also protects against bot attacks, credential stuffing, API abuse, and application-layer DDoS attacks. Our intelligent risk scoring and machine learning algorithms detect both known attack signatures and anomalous behavior patterns.
How much does a web application firewall cost?
Azion WAF uses transparent usage-based pricing where you only pay for requests analyzed by the WAF. Start with $300 in free credits to test the service with no credit card required. Pricing scales with your traffic volume, with no hidden fees, infrastructure costs, or vendor lock-in. Our distributed edge computing architecture eliminates the need for centralized cloud infrastructure, reducing costs and latency. Enterprise plans include custom rule development, dedicated support, and volume discounts. Most customers save 40-60% compared to traditional enterprise WAF solutions while eliminating infrastructure management costs entirely.
Do I need a WAF if I already have a CDN or load balancer?
Yes, CDNs and load balancers do not provide application-layer security against web attacks. While CDNs optimize content delivery and load balancers distribute traffic, they cannot detect or block SQL injection, XSS, or other OWASP Top 10 threats. Azion WAF integrates directly with our CDN and edge computing platform, providing comprehensive security without adding latency. You get both performance optimization and enterprise-grade protection in a single platform, with security events analyzed before requests reach your origin servers.











