Protect
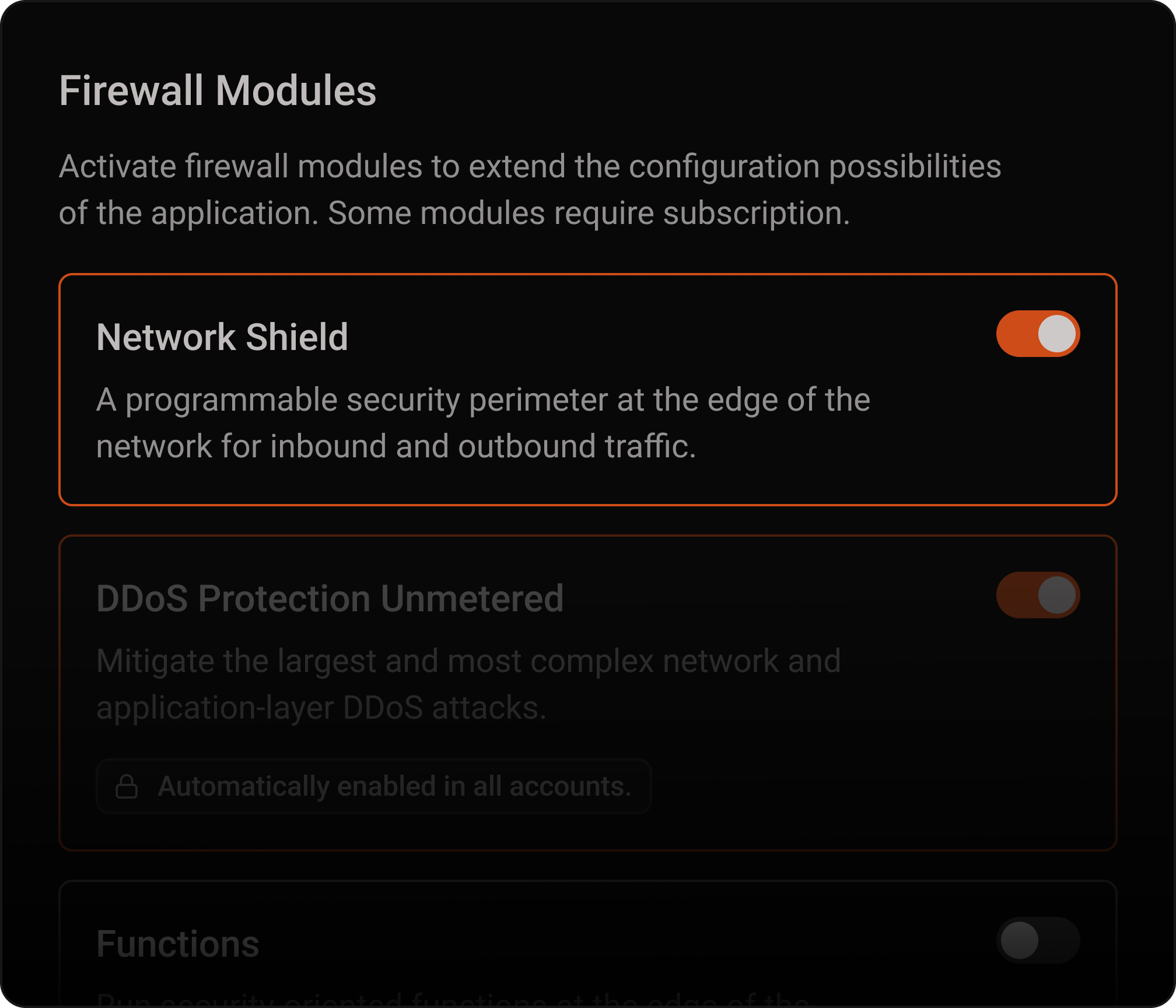
Network Shield
Create a programmable security perimeter on the Azion Web Platform's distributed architecture to protect applications, APIs, and networks in any environment — multi-cloud, hybrid, or on-premises.
Advanced mitigation
Use network lists of IP addresses, geographic locations, and ASNs and the power of the Rules Engine to harden applications, content, and infrastructure.
Multi-cloud and On-Prem
Protect your applications, APIs, and networks wherever they are hosted: in multi-cloud, on-premises, or hybrid environments.
Reduce Costs
Block unwanted traffic on the distributed infrastructure before it consumes resources on your origin.
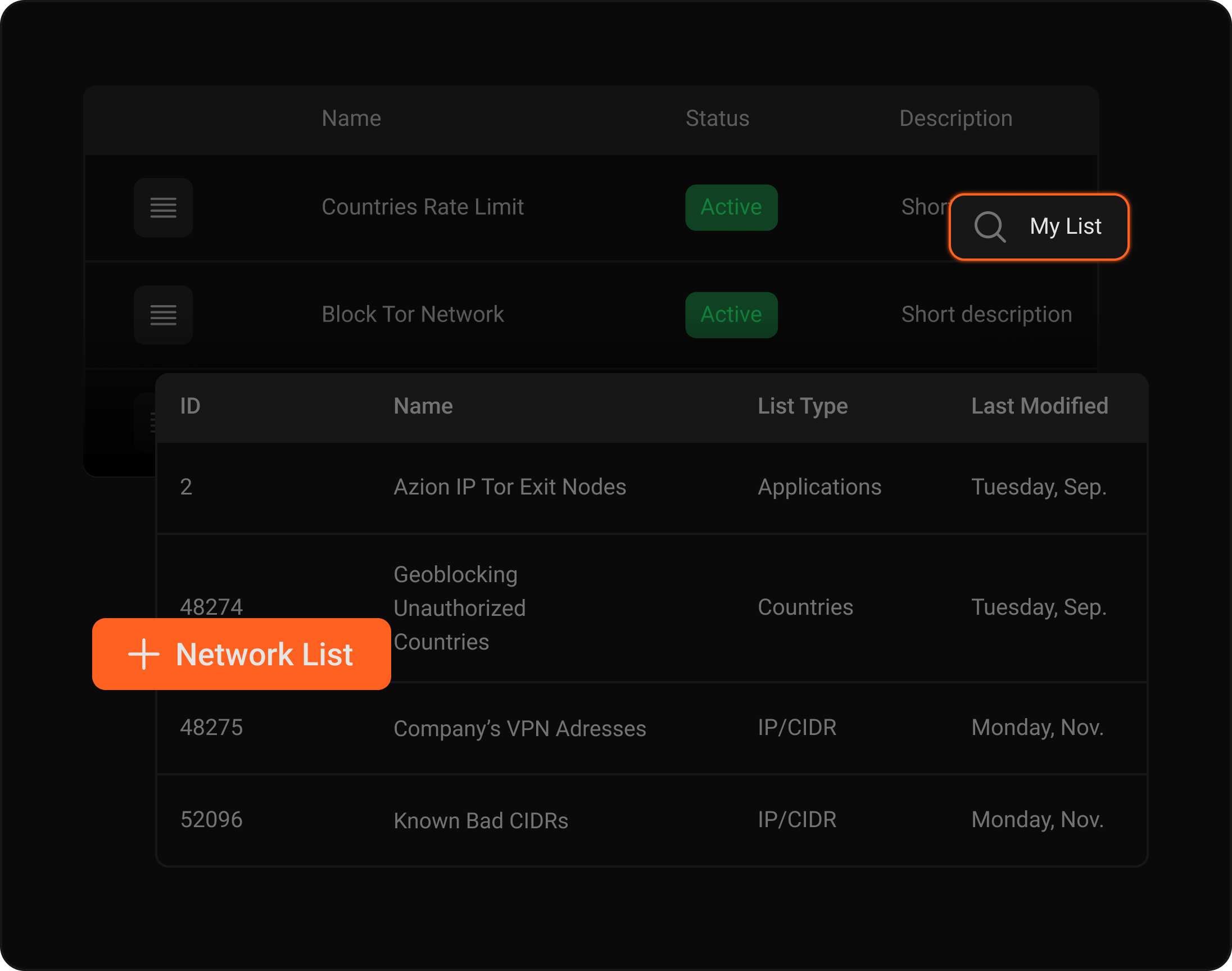
Network Lists for programmable ACLs
Define access policies with lists that combine IP addresses, geolocation, ASNs, and reputation.
Reference these lists directly in the Firewall and ensure updates are propagated automatically without causing service interruption
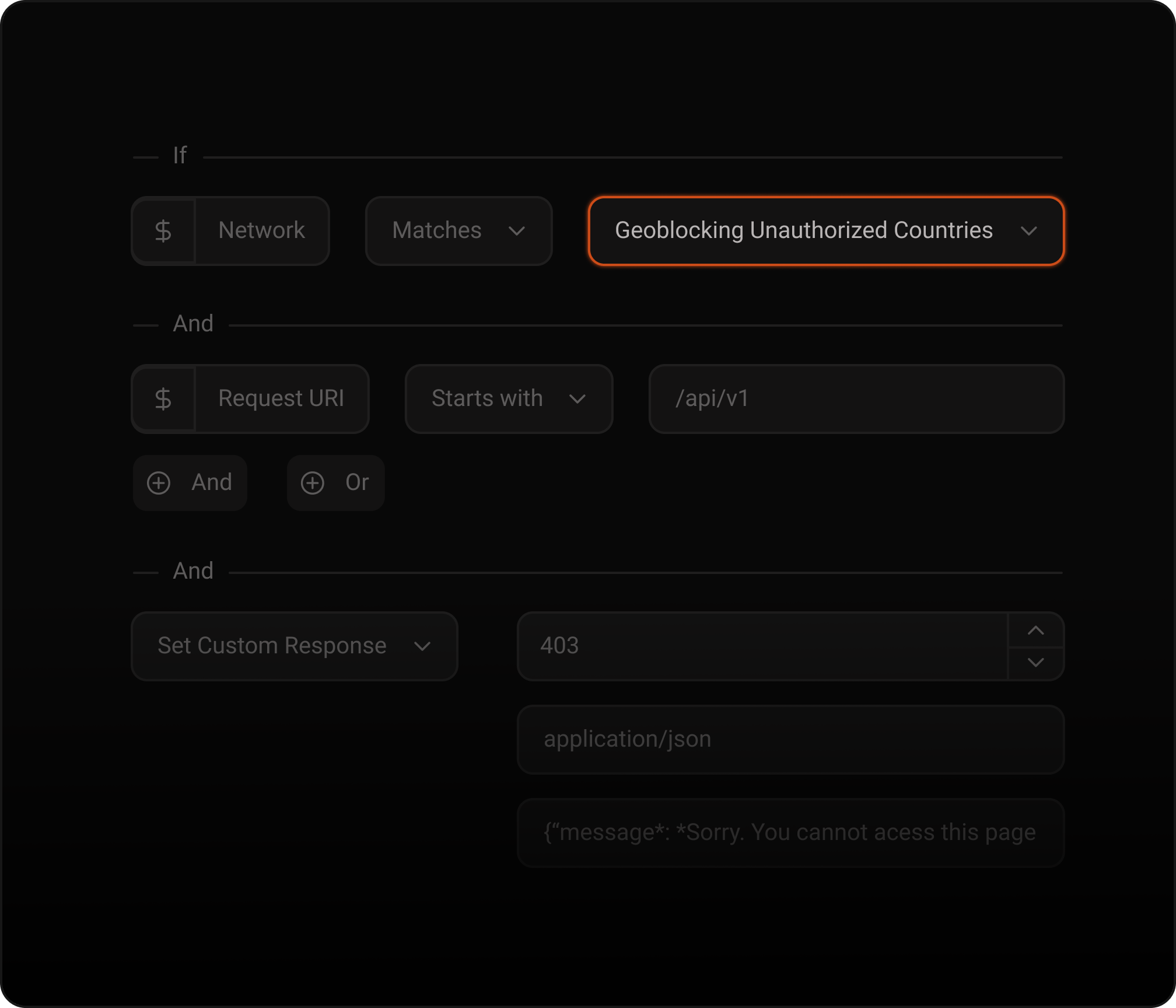
Simplified security with rule-based traffic control
Simplify security management with a centralized catalog of ACLs and apply actions based on custom rules.
Segment access by region, trusted address lists, allow search crawlers without opening gaps, and keep policies consistent by sharing network lists across multiple firewalls.
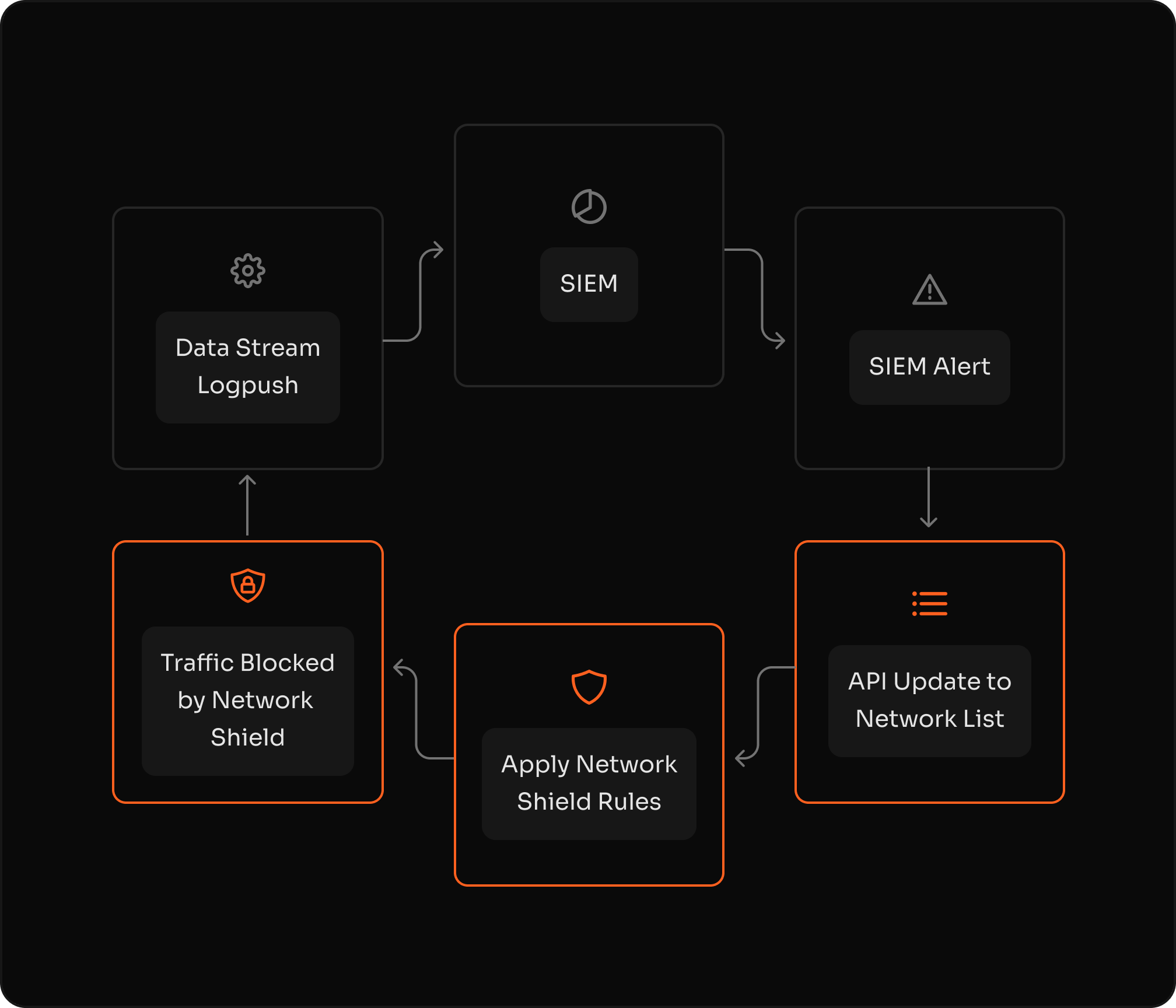
Threat response through automation
Stream events in real time to your SIEM and use automated playbooks to update Network Lists via API with effects in seconds.
Orchestrate dynamic decisions using Azion Functions to adapt the risk response and implement programmable blocks on each request.