In this post about web application firewall (WAF), we list its ability to combat the OWASP Top 10 security risks as one of the major benefits (and requirements) of this type of solution.
OWASP Top 10 is a project conducted by the OWASP® Foundation with the collaboration of security experts and web application developers used as a reference by security experts and companies around the world.
Currently, the OWASP Top 10 Risks document is comprised of the following threats:
- A1:2021 - Broken Access Control;
- A2:2021 - Cryptographic Failures;
- A3:2021 - Injection;
- A4:2021 - Insecure Design;
- A5:2021 - Security Misconfiguration;
- A6:2021 - Vulnerable and Outdated Components;
- A7:2021 - Identification and Authentication Failures;
- A8:2021 - Software and Data Integrity Failures;
- A9:2021 - Security Logging and Monitoring Failures;
- A10:2021 - Server-Side Request Forgery (SSRF).
Next, we’ll see some details about each of these risks and how Azion’s WAF can be a great ally to prevent them.
A1:2021 | Broken Access Control
Access control is a security mechanism used to restrict resource accessibility and determine user permissions. Breaking access control means that unauthorized users have accessed confidential information, for example.
This failure usually occurs when the application does not restrict access to data or system functionality, resulting in unauthorized disclosure of information, modification or destruction of data, or execution of tasks that would only be up to the system administrator.
Access Control Optimization with Azion’s WAF
By using the WAF as an additional security layer, it’s possible to anticipate threats to the access control system and define a set of instantaneous traffic analysis for each potentially targeted component of the application, such as APIs and user authentication pages.
Another important means of prevention is the implementation of a zero trust security model, so that each user has only the minimum necessary permissions within a system.
A2:2021 | Cryptographic Failures
Cryptographic flaws are due to the lack (or inefficiency) of encryption, and can result in exposure of data such as credit card numbers and personal user information.
According to OWASP, there are several situations classified in Notable Common Weakness Enumerations (CWEs)[1] that lead to data exposure, such as:
- CWE-259 -Use of hard-coded password: Occurs when information associated with authentication is exposed in the body of the script, which can be easily extracted by any user of the application;
- CWE-327 - Use of broken/dangerous encryption algorithm or protocol: This flaw is challenging because producing a secure algorithm is difficult and, when it’s not updated to follow the rapid technological advances and the increase in computational power, the level of protection provided is no longer the same;
- CWE-331 - Insufficient entropy: In the information security context, entropy is random information collected by the operating system to randomly generate cryptographic keys. In this case, insufficient entropy is a depletion of new information to generate unique cryptographic keys, and key duplication may be one of the consequences in this case.
The number and variety of factors that result in encryption failures explain why this risk ranks second on the list.
Data Protection with WAF
There are many ways to prevent cryptographic flaws from compromising data security, and the main one is to protect data with end-to-end encryption (also known as E2EE).
Extending encryption to web traffic using the TLS (Transport Layer Security) protocol is also very important for that. With Edge Application, you can do this in just five steps.
In addition, our WAF has a function for analyzing requests in search of certain characters, strings and patterns that characterize potentially malicious traffic. With a blocking method based on scoring instead of signatures, Azion’s WAF ensures that not even zero-day threats can exploit your application and gain access to data.
A3:2021 | Injection
An injection attack consists of injecting malicious code into an application in order to gain control over it or steal the data stored in it.
There are two common types of injection; the first one is based on query languages, such as SQL injection (SQLi), and the second on scripting, such as Cross-Site Scripting (XSS), whose impacts vary between:
- authentication bypass;
- cache poisoning;
- loss, theft or breach of data;
- denial of service;
- data leak.
This type of attack is capable of compromising an entire system by making the application behave unexpectedly. The consequences can happen both on the server and on the client side.
Automated Injection Blocking
By creating a WAF Rules Set on the Azion platform, the user has access to several specific settings applicable to some types of threats.
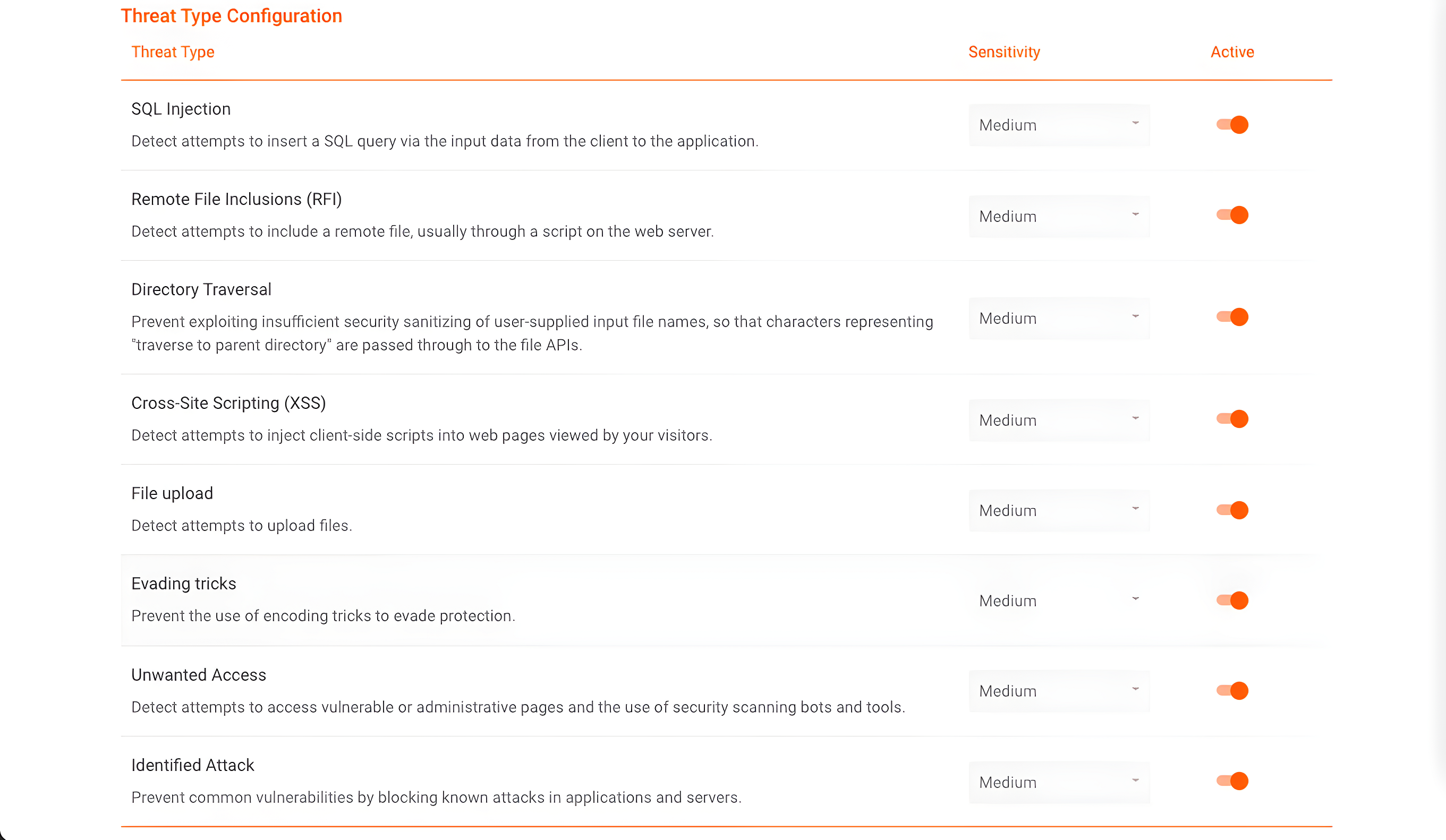
In the image above you can verify that it’s possible to configure the WAF to automatically detect and block SQL injections and Cross-Site Scripting, and adjust sensitivity levels that will define the severity of the WAF when analyzing whether the request is a threat.
A4:2021 | Insecure Design
Insecure design refers to applications that are not built using strict security standards. This causes failures to be present throughout the development cycle of an application.
One of the best analogies to illustrate insecure design is building a house. When construction doesn’t follow best practices, it’s certain that problems will arise sooner or later.
The consequences of insecure design in web applications can surface quickly, as all components can have some type of vulnerability, including in the transport and network layers.
Azion WAF Integration with CI/CD Pipelines
Azion’s Web Application Firewall was designed to meet the most complex security demands and also to simplify testing and validation processes for secure software.
Through predefined rules, WAF can be integrated with existing CI/CD pipelines and, from there, automate code validations and tests, which favors agile development and compliance optimization.
It’s important to highlight that automation is just one of the possibilities to prevent insecure design. On our full-stack edge platform, customers build environments to test various security scenarios and thus ensure the effectiveness of firewall rules without the need to put the application into production.
A5:2021 | Security Misconfiguration
According to OWASP, 90% of applications were tested for some security misconfiguration, with a 4% incidence rate and more than 208,000 occurrences of CWEs that this risk encompasses. How can this be explained?
Modern applications are complex and highly customizable. Therefore, as large-scale changes are implemented without a meticulous care for security, there’s a tendency for vulnerabilities to surface constantly.
In addition, errors may occur at any level or component of the application, such as containers, databases and APIs—not by chance, 41% of organizations suffered some type of security incident with APIs in 2021[2].
Building Restrictive Rules for an Enhanced Security Configuration
In addition to integration with existing CI/CD pipelines, Azion’s WAF works with restrictive rule sets ideal for a robust security setup.
Based on the Match Pattern parameters (comparison condition, string or regex to be searched for in the request), which can be broadly applied or assigned to a path, the WAF allows validating:
- HTTP headings;
- POST arguments;
- GET arguments;
- file name.
Simply, the user is able to establish advanced firewall rules to protect critical parts of applications, including in response to events and discoveries.
For instance, if a suspected XSS attack was identified in an application service, the team of experts can improve the WAF algorithm with more precise rules to protect it.
FourBank’s success story is a good illustration of this capability of Azion’s WAF. In it, a DDoS attack that exploited the APIs was mitigated using a WAF rule.
A6:2021 | Vulnerable and Outdated Components
This risk refers to applications composed of libraries, frameworks and other third-party components that are outdated or have known vulnerabilities.
The impact of this is their exposure to different attack vectors, such as injections and remote execution of malicious code. This often happens because developers are not aware of the software update or the vulnerabilities in it.
There is also a problem linked to monolithic applications, as since any part of the application can be affected by the implementation of a component, the update is considered a risk and, therefore, neglected.
Updates and Security Patches with Azion’s WAF
As Azion’s WAF delivers security at the edge, the solution simplifies the update of virtual rules and patches, which can be deployed using Edge Functions.
One of the benefits of patches is that they minimize the need for custom code changes and also minimize friction between the development and security teams.
More than only known vulnerabilities, Azion’s WAF blocks zero-day attacks with a degree of efficiency that several global vendor solutions have not achieved. Want to know more? Discover how Azion’s WAF was not affected by the WAF Bypass.
A7:2021 | Identification and Authentication Failures
Identification and authentication failures occur due to the absence of protection mechanisms to validate the user’s identity, such as Multi-Factor Authentication (MFA), and blocking attacks such as credential stuffing and brute force.
Other common causes are applications that allow the use of weak passwords or that are stored in an insecure way, such as in text files without proper formatting or encryption.
Enhanced Authentication Mechanism with WAF Rules and Edge Functions
In addition to the WAF resources to improve access control, which are perfectly applicable to this context, Azion offers access to a marketplace with specific solutions for:
- facial recognition;
- URL validation;
- IP reputation;
- security token.
These are great complements to authentication mechanisms and can be implemented in a few steps via edge functions.
To ensure that passwords and access credentials are stored securely, the WAF can be used to create extremely restrictive sets of rules with high granularity, as explained above.
Besides that, WAF rules can be enhanced with rate limiting and then prevent attacks like account takeover (ATO) and fraud such as the use of credit cards and login credentials acquired on the dark web.
A8:2021 | Software and Data Integrity Failures
Software and data integrity failures are characterized by the use of data or applications without an adequate check or verification process. Common examples are applications made up of libraries, repositories and plugins from untrusted sources.
According to OWASP, another problem that contributes to the emergence of these failures is the automatic update functionality activated in most applications, as updates are downloaded without completely checking their integrity.
Filtering and Validating Requests with WAF
The settings adjusted by type of threat found in Azion’s WAF help to prevent attacks such as remote file inclusions (RFI) and directory traversal, ensuring that only verified requests are delivered.
Implementing secure software development best practices is also an important step in preventing integrity failures. Therefore, the very integration with the CI/CD processes contributes significantly to the construction of more secure code.
Compliance optimization is also a relevant point in this regard. After all, when complying with requirements such as PCI DSS and SOC 3, it is only natural that the application is better protected in terms of design and configuration.
A9:2021 | Security Logging and Monitoring Failures
Security logging and monitoring are basic requirements for detecting and responding to existing vulnerabilities in an application. In addition, such activities are essential for:
- auditing critical events such as logins and financial transactions;
- suspicious activity detection and mapping;
- penetration tests and security checks;
- development of an event response plan.
When security logging and monitoring fail, the organization not only fails to evolve its defense line, but ends up exposing user data and putting service availability at risk.
Monitoring and Observability
Azion’s WAF contributes to security monitoring by acting both as an Intrusion Detection System (IDS), analyzing and monitoring traffic in search of threats, and as an Intrusion Prevention System (IPS), proactively blocking traffic using a scoring-based detection method.
In terms of observability, the WAF provides event logs that can be accessed in Real-Time Metrics.
“When everything started to travel through Azion, we gained a better understanding of everything that happens in the applications, enabling us to make action plans to deal with certain situations if they appear”
Jefferson Bornhausen, IT Director at FourBank
For a more complete data experience, your security team can use Azion’s Data Stream or our GraphQL Events API to feed your SIEM platforms with raw WAF event data.
A10:2021 | Server-Side Request Forgery (SSRF)
Server-Side Request Forgery (SSRF) is a vulnerability that occurs when the web application sends HTTP requests to an unexpected location, so the attacker exploits that touchpoint to gain access to data and services.
Typically, the malicious request induces the server to connect to internal application services, such as APIs, and provide direct access to the administrative interface through which privileges are granted to the user.
A successful SSRF attack results in the exposure of the organization’s internal data and opens up a space for a variety of other attacks to be practiced, such as DDoS and remote code execution.
WAF as an Additional Layer of Security
As an SSRF attack is characterized by the connection with the origin server, the edge computing architecture through which Azion’s WAF works can be considered a security perimeter by itself.
However, as demonstrated throughout this content, the WAF enables the creation of custom rules that can be implemented in specific parts of your application, according to the business needs, and prevent malicious requests from gaining access to them.
Now that you know how Azion’s WAF helps tackling the OWASP Top 10 security risks, how about testing it in your application? By creating a free account, you’ll receive $300 in service credits to try out our edge computing platform.