For many CISOs and other security professionals today, the decision to move to zero trust is an easy one—the question that remains is how to get there. Microsoft’s recent report on zero trust revealed that 96% of security professionals surveyed believe that zero trust is very or somewhat critical to their enterprise’s security.[1] But despite this clear consensus, the survey showed that only 76% of those surveyed have begun implementing zero trust solutions, and many of those who have are still struggling with practical concerns like education and skills gaps, getting budgets approved, finding the right vendors, and integrating solutions.
So how can security professionals overcome the barriers to zero trust and gain a strong return on investment? This blog will explain the components and reference architecture needed for effective zero trust security, examine the barriers to implementation, and discuss how the right vendor can help simplify integration and reduce costs.
What Are the Components of Zero Trust Architecture?
In the past few years, the increased popularity of remote work and an accompanying shift to the cloud have popularized the zero trust model. But although most security professionals are familiar with the concept of zero trust, research shows that the practical implications are far less clear. NIST defines two basic protections needed for zero trust: establishing least-privilege access to resources to limit horizontal attacks and continually authenticating and authorizing requests to ensure not only the identity of authorized users, applications, services and devices, but their security posture during each access.[2]
The diagram below illustrates how the zero trust model enforces these protections for each individual access request. Each request is treated as untrusted until it passes through a policy decision point (PDP) and policy enforcement point (PEP) to the implicit trust zone. The PDP determines if the request is authorized, logs the decision to admit or deny access, and authenticates authorized requests; the PEP enables, monitors, and eventually terminates connections within the implicit trust zone, based on updates from the policy decision point.
 Note that this process is enacted for each access request, regardless of the user, device, or service making the request, and the inherent trust zone must be as small as possible based on the business need. This allows for authorization to be continually adapted based on context and behavior; a necessity given the flexibility of today’s workforce, where:
Note that this process is enacted for each access request, regardless of the user, device, or service making the request, and the inherent trust zone must be as small as possible based on the business need. This allows for authorization to be continually adapted based on context and behavior; a necessity given the flexibility of today’s workforce, where:
- enterprises may not own or be able to configure employee or contractor devices;
- remote users and services may attempt access through insecure networks; and
- enterprise resources may exist on the cloud or other infrastructure not owned or maintained by the enterprise.
Zero Trust Architecture in Action
To better illustrate how the process of authorization and authentication works in a zero-trust system, consider the following example using a widely adopted tool for policy decision and enforcement: a web application firewall (WAF).
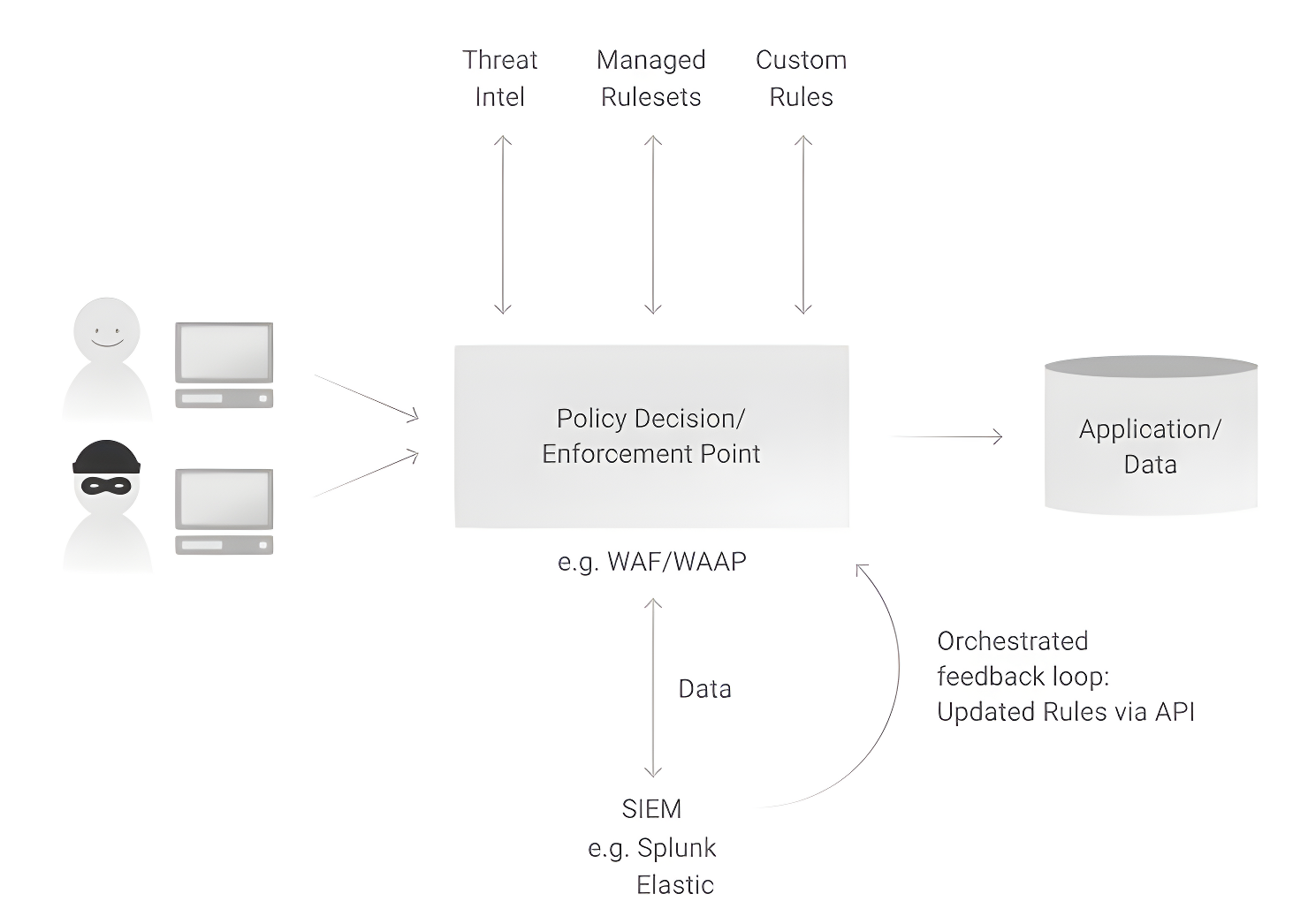 In the diagram above, we have two scenarios: an authorized user and a malicious user, both of whom are attempting to access a resource. The WAF serves as the policy decision and enforcement point, which uses criteria such as managed rule sets (designed to block OWASP Top 10 threats and other common threats), custom rules (based on industry regulations and the business need for access to certain resources), and threat intelligence (rules based on internal or external analyses of threats based on information about how threats are being carried out, resources used to launch attacks, and a business’s specific risks and vulnerabilities) to determine whether to block or allow a request.
In the diagram above, we have two scenarios: an authorized user and a malicious user, both of whom are attempting to access a resource. The WAF serves as the policy decision and enforcement point, which uses criteria such as managed rule sets (designed to block OWASP Top 10 threats and other common threats), custom rules (based on industry regulations and the business need for access to certain resources), and threat intelligence (rules based on internal or external analyses of threats based on information about how threats are being carried out, resources used to launch attacks, and a business’s specific risks and vulnerabilities) to determine whether to block or allow a request.
Through integration with a business’s SIEM via Data Stream, WAF rules can be updated in real time via API, creating an orchestrated feedback loop that monitors and manages access on an ongoing basis. This step-by-step process can be seen below:
- A security policy is defined in the WAF
- Monitoring tool detects user violation of this policy
- Monitoring tool creates alert/event
- Details of alert/event are sent to SIEM
- Network list of abusive users is updated via API and orchestration
- User is stopped from violating policies
In addition, privileged access, such as admin rights to a security solution (which could, for example, give users the ability to update or change rules in a WAF), can be enhanced with tools like multi-factor authentication, providing an extra layer of security to ensure that only authorized users can gain access to controls that would grant them wide permissions to entire systems and put business’s most valuable assets at risk.
Choosing Zero-Trust Solutions
One of the top barriers to zero trust listed by security professionals in surveys by Microsoft[1] and Fortinet[3] is difficulty selecting vendors, which is compounded by budgetary, technological, and resource constraints like the difficulty of justifying and securing costs needed to purchase solutions, the lack of talent or education needed to implement solutions, and the ability to integrate solutions with other technologies. This means that it is absolutely essential to choose a vendor that makes implementation as simple and cost-effective as possible.
To reduce costs, businesses should look for vendors that:
- offer integration assistance and 24/7 engineer-to-engineer support;
- leverage open standards to simplify integration and reduce the threat of vendor lock-in;
- reduce cost by charging per request, which eliminates upfront costs from provisioning and enables decision makers to easily understand the return on investment; and
- block at the edge, which reduces the cost per blocking by requiring less bandwidth and minimizes risk by eliminating threats to origin servers.
To find out more about Azion can help your business build out its zero-trust security solutions, check out our security success stories, or to receive a free analysis of your security posture, contact one of our experts today.
References
[1] Microsoft, Zero Trust Adoption Report
[2] NIST, Zero Trust Architecture
[3] Fortinet, Survey Reveals Challenges of Zero Trust Implementation








