A zero-day exploit has been recently discovered in multiple versions of the Apache Log4j library that allows for unauthenticated remote code execution by logging certain strings. The vulnerability, which was published as CVE-2021-44228 on Friday, December 10, poses a severe risk due to the ubiquity of the popular Java-based logging library, how easy it is to exploit, and the impact of the attack, which gives unauthorized users full server control. To ensure that our customers are protected against this critical vulnerability, we’d like to share what we’ve done to guard against these attacks and what steps Azion users should take to ensure they are protected.
What Is It?
The exploit is a type of attack known as a remote code execution (RCE), one of the most dangerous types of vulnerabilities as it allows attackers to execute malicious code from attacker-controlled servers. This is possible in most versions of Log4j version 2, which added JDNI lookups, a Java API that lets users interface with LDAP and DNS to look up data and resources. However, JDNI lookups were not restricted, allowing URIs to be returned that point to and load untrusted Java classes, enabling the execution of third-party code from malicious LDAP servers and other JNDI-related endpoints when message lookup substitution is enabled. This attack requires very little skill on the part of the attacker, as the attack can be triggered with only a single line of text.
Apache has released a patch that disables this behavior by default from log4j 2.15.0, as well as a subsequent patch, log4j 2.16.0, which also fixes CVE-2021-45046, a more recently found critical vulnerability. However, this threat is still developing, and Apache’s security team is continuing to look into new issues as they arise. It is recommended that all organizations using the log4j library upgrade to the newest version (currently 2.17.1) immediately, and continue to check for updates on this developing threat.
Who is Affected?
CVE-2021-44228 affects almost all versions of Log4j version 2 from 2.0-beta9 to 2.14.1. Log4j is used by millions of applications for logging, including Apple, Twitter, Redis, and Elasticsearch, just to give you an idea of its ubiquitousness. A Github community resource provides a growing list of vulnerable and impacted software and components. The exploit is reportedly already being used by cryptocurrency miners and botnets, with attackers using a “spray and pray” approach that puts any organization with the vulnerability at risk.
Azion’s Response
At Azion, our Security team jumped into action as soon as the CVE was confirmed. By Saturday, Dec 11, 2021, 8:40 PM PST (UTC-8), an update to our WAF security rules was pushed out across our entire network to protect all of our WAF customers from CVE-2021-44228. (This rule update also protects against CVE-2021-45046 and its variants, for our WAF customers with Remote File Inclusion (RFI) enabled, at any sensitivity level!)
What Azion WAF Customers Need To Know
To ensure your Azion WAF is preventing this exploit, follow these steps if you haven’t already.
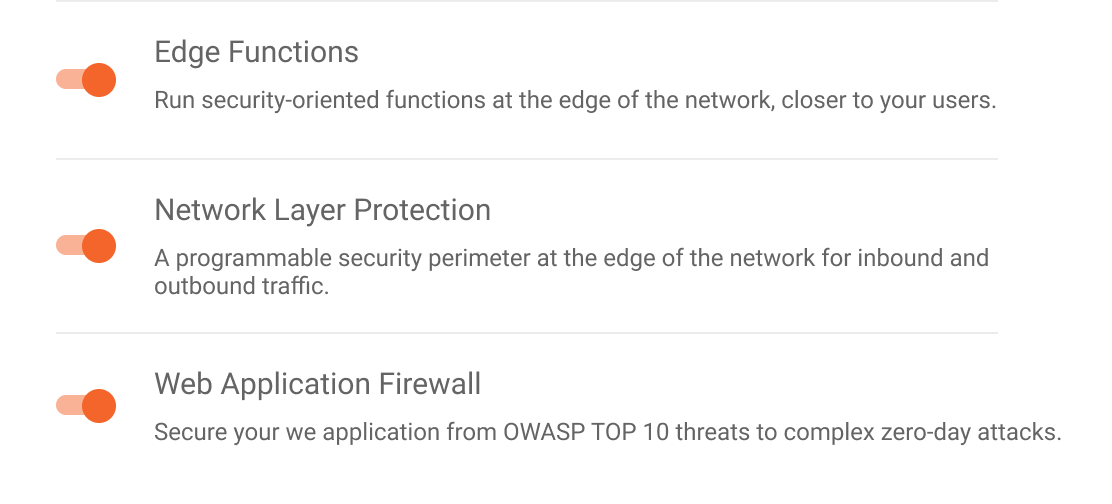
Step 1: Create a WAF configuration if you don’t already have one, and be sure Web Application Firewall is enabled on your desired Azion Edge Firewall:
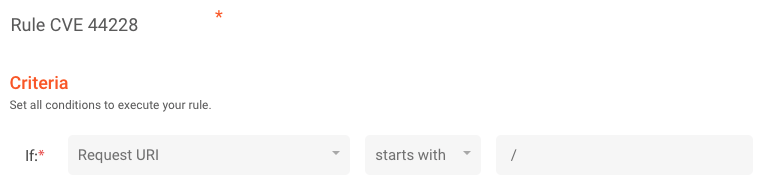
Step 2: Create a simple rule to trigger WAF with the following criteria:
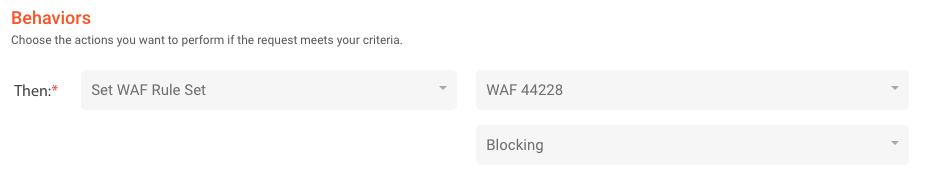
Step 3: With behavior as below, where “WAF 44228” is an arbitrary name for your WAF configuration. Be sure to set the behavior to Blocking mode.
That’s it! And we’re also happy to provide help to any customers who may need it, just email support@azion.com.
Conclusion
This severe and pervasive exploit has gained substantial attention since its discovery, and with good reason: the critical threat poses a huge risk to organizations worldwide as opportunistic cybercriminals attempt to profit from it. As the threat quickly spreads across the Internet, you can expect to see innumerable variations on attack strings, requiring constant updates for traditional WAFs, which block attacks based on known signatures that are easy for attackers to manipulate. To ensure that your team is protected, you should immediately take recommended actions such updating affected software as outlined in CVE-2021-44228, ensuring your WAF is set to block the exploit, and ensuring your security operations center is taking action to follow up on all RCE alerts. If your organization is at risk and would like help protecting against this vulnerability, you can contact our experts to find out more.








